VRF question for CCNP
-
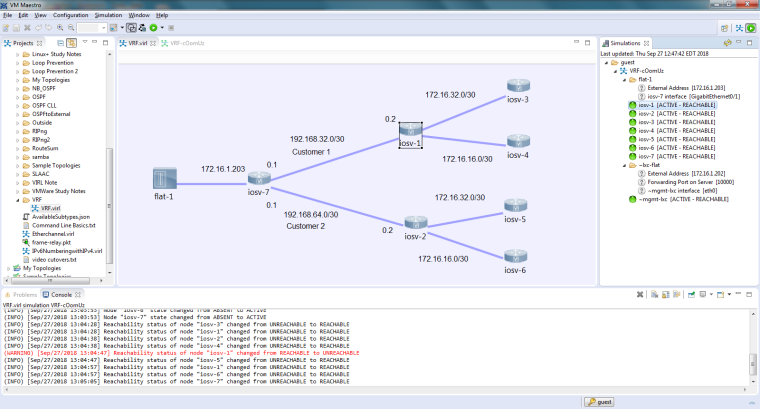
My Fortinet 60E has static routes back to my Cisco VIRL.
iosv-7#sh run
Building configuration...Current configuration : 4207 bytes
!
! Last configuration change at 16:21:45 UTC Thu Sep 27 2018
!
version 15.6
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname iosv-7
!
boot-start-marker
boot-end-marker
!
!
vrf definition Mgmt-intf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
enable password cisco
!
no aaa new-model
!
!
!
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
!
!
!
!
!
!
!
ip vrf customer1
!
ip vrf customer2
!
!
!
!
no ip domain lookup
ip domain name virl.info
ip cef
ipv6 unicast-routing
ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
username cisco privilege 15 secret 5 $1$HfX0$AB3o8OYGbq7yhl7Cs7l9v/
!
redundancy
!
no cdp run
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback0
description Loopback
no ip address
!
interface GigabitEthernet0/0
description OOB Management
vrf forwarding Mgmt-intf
ip address 10.255.7.31 255.255.0.0
duplex full
speed auto
media-type rj45
!
interface GigabitEthernet0/1
description to flat-1
ip address 172.16.1.203 255.255.255.0
duplex full
speed auto
media-type rj45
!
interface GigabitEthernet0/2
description to iosv-1
ip vrf forwarding customer1
ip address 192.168.32.1 255.255.255.252
duplex full
speed auto
media-type rj45
!
interface GigabitEthernet0/3
description to iosv-2
ip vrf forwarding customer2
ip address 192.168.64.1 255.255.255.252
ip ospf 2 area 0
duplex full
speed auto
media-type rj45
!
router ospf 1 vrf customer1
router-id 0.0.7.1
network 192.168.32.0 0.0.0.3 area 0
default-information originate always
!
router ospf 2 vrf customer2
router-id 0.0.7.2
network 192.168.64.0 0.0.0.3 area 0
default-information originate always
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 172.16.1.1
ip route vrf customer1 0.0.0.0 0.0.0.0 172.16.1.1 global
ip route vrf customer2 0.0.0.0 0.0.0.0 172.16.1.1 global
ip ssh server algorithm encryption aes128-ctr aes192-ctr aes256-ctr
ip ssh server algorithm authentication password
ip ssh client algorithm encryption aes128-ctr aes192-ctr aes256-ctr
!
ipv6 ioam timestamp
!
!
!
control-plane
!
banner exec ^C
- IOSv is strictly limited to use for evaluation, demonstration and IOS *
- education. IOSv is provided as-is and is not supported by Cisco's *
- Technical Advisory Center. Any use or disclosure, in whole or in part, *
- of the IOSv Software or Documentation to any third party for any *
- purposes is expressly prohibited except as otherwise authorized by *
- Cisco in writing. *
**************************************************************************^C
banner incoming ^C
- IOSv is strictly limited to use for evaluation, demonstration and IOS *
- education. IOSv is provided as-is and is not supported by Cisco's *
- Technical Advisory Center. Any use or disclosure, in whole or in part, *
- of the IOSv Software or Documentation to any third party for any *
- purposes is expressly prohibited except as otherwise authorized by *
- Cisco in writing. *
**************************************************************************^C
banner login ^C
- IOSv is strictly limited to use for evaluation, demonstration and IOS *
- education. IOSv is provided as-is and is not supported by Cisco's *
- Technical Advisory Center. Any use or disclosure, in whole or in part, *
- of the IOSv Software or Documentation to any third party for any *
- purposes is expressly prohibited except as otherwise authorized by *
- Cisco in writing. *
**************************************************************************^C
!
line con 0
password cisco
line aux 0
line vty 0 4
exec-timeout 720 0
password cisco
login local
transport input telnet ssh
!
no scheduler allocate
!
end
iosv-7#
iosv-7#From 60E:
FWF60E4Q16000229 # exec traceroute 192.168.32.1traceroute to 192.168.32.1 (192.168.32.1), 32 hops max, 3 probe packets per hop, 72 byte packets
1 172.16.1.203 2.452 ms 2.353 ms 1.987 ms
2 172.16.1.1 3.419 ms 1.091 ms 1.935 ms
3 172.16.1.203 4.265 ms 5.506 ms 2.001 ms
4 172.16.1.1 0.655 ms 0.943 ms 1.099 ms
5 172.16.1.203 4.420 ms 5.736 ms 3.449 ms
6 172.16.1.1 2.073 ms 1.866 ms 2.750 ms
7 172.16.1.203 3.889 ms 7.043 ms 3.331 ms
8 172.16.1.1 2.390 ms 3.839 ms 2.348 ms
9 172.16.1.203 5.872 ms 5.165 ms 4.879 ms
10 172.16.1.1 3.187 ms 3.522 ms 3.734 ms
11 172.16.1.203 5.144 ms 5.392 ms 4.754 ms
12 172.16.1.1 3.511 ms 3.707 ms 4.145 ms
13 172.16.1.203 6.651 ms 6.003 ms 5.832 ms
14 172.16.1.1 4.322 ms 4.550 ms 5.100 ms
15 172.16.1.203 6.373 ms 6.314 ms 5.861 ms
16 172.16.1.1 4.888 ms 5.228 ms 5.541 ms
17 172.16.1.203 8.368 ms 9.494 ms 7.112 ms
18 172.16.1.1 6.047 ms 7.554 ms 5.993 ms
19 172.16.1.203 7.710 ms 7.416 ms 7.195 ms
20 172.16.1.1 5.736 ms 6.759 ms 6.782 ms
21 172.16.1.203 9.385 ms 8.447 ms 8.231 ms
22 172.16.1.1 6.700 ms 7.223 ms 6.432 ms
23 172.16.1.203 10.192 ms 8.615 ms 11.718 ms
24 172.16.1.1 7.385 ms 7.690 ms 7.222 ms
25 172.16.1.203 10.012 ms 9.779 ms 9.516 ms
26 172.16.1.1 7.946 ms 8.692 ms 8.871 ms
27 172.16.1.203 10.041 ms 10.367 ms 9.682 ms
28 172.16.1.1 8.389 ms 8.663 ms 9.707 ms
29 172.16.1.203 10.295 ms 10.897 ms 10.741 ms
30 172.16.1.1 9.490 ms 9.283 ms 9.862 ms
31 172.16.1.203 11.674 ms 11.227 ms 11.908 ms
32 172.16.1.1 9.769 ms 9.952 ms 10.004 ms
From ios-7
iosv-7#ping 172.16.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/6 ms
iosv-7#I can ping from ios-7 to the 60E address 172.16.1..1 . I can ping from 60E to 172.16.1.203.
FWF60E4Q16000229 # exec ping 172.16.1.203
PING 172.16.1.203 (172.16.1.203): 56 data bytes
64 bytes from 172.16.1.203: icmp_seq=0 ttl=255 time=2.6 ms
64 bytes from 172.16.1.203: icmp_seq=1 ttl=255 time=2.2 ms
64 bytes from 172.16.1.203: icmp_seq=2 ttl=255 time=2.4 ms
64 bytes from 172.16.1.203: icmp_seq=3 ttl=255 time=2.7 ms
64 bytes from 172.16.1.203: icmp_seq=4 ttl=255 time=2.4 ms
--- 172.16.1.203 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 2.2/2.4/2.7 ms
iosv-7#sh ip route vrf customer1
Routing Table: customer1
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfRGateway of last resort is 172.16.1.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 172.16.1.1
172.16.0.0/30 is subnetted, 2 subnets
O 172.16.16.0 [110/2] via 192.168.32.2, 00:31:06, GigabitEthernet0/2
O 172.16.32.0 [110/2] via 192.168.32.2, 00:31:06, GigabitEthernet0/2
192.168.32.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.32.0/30 is directly connected, GigabitEthernet0/2
L 192.168.32.1/32 is directly connected, GigabitEthernet0/2
iosv-7#
iosv-7#
iosv-7#
iosv-7#sh ip route vrf customer2Routing Table: customer2
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfRGateway of last resort is 172.16.1.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 172.16.1.1
172.16.0.0/30 is subnetted, 1 subnets
O 172.16.16.0 [110/2] via 192.168.64.2, 00:31:11, GigabitEthernet0/3
192.168.64.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.64.0/30 is directly connected, GigabitEthernet0/3
L 192.168.64.1/32 is directly connected, GigabitEthernet0/3
iosv-7# -
iosv-7#ping 172.16.32.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.32.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
iosv-7#ping 172.16.32.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.32.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
iosv-7#iosv-7#ping 192.168.32.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.32.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
iosv-7#
iosv-7#
iosv-7#ping 192.168.32.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.32.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
iosv-7#Any ideas? It is like I can get from the WAN side to the VRF side on ios-v7
-
Is the following what you intended for both vrfs?
ip route 0.0.0.0 0.0.0.0 172.16.1.1
ip route vrf customer1 0.0.0.0 0.0.0.0 172.16.1.1 global
ip route vrf customer2 0.0.0.0 0.0.0.0 172.16.1.1 global -
172.16.1.1 is the firewall port. It takes you out to the real world. So both Customer1 and Customer2 will go to my TFTP server.
-
iosv-7#sh run | redirect tftp://192.168.1.240/iosv7-shrun.txt
!
iosv-7#This copies the sh run to my workstation tftp server.
-
Can both customer 1 and customer 2 reach it that address heading outbound.
on the pings, you can try and source the address to something within your customer 2 and see if it works. If it does, then it's the vrf that is stopping you as it should.
You may also want to just ping from a iosv-5 and from iosv-6. are those making it your ping dst.
-
They can't reach 192.168.1.203 even from Customer1 or Customer2. I posted to Cisco Learning Network. One guy posted an interesting article on VRF Fun. He said place global routes on IOSv-7 pointing towards customer1 and customer2.
https://learningnetwork.cisco.com/message/699025#699025
Hi Jeffrey,
If you want to solve this task without NAT then you need to populate the global routing table with the routes pointing to particular VRFs. Think of this: Packets from R4 will arrive on R1's f0/0 interface, and since this interface is placed into the global routing table, the packets' fate will be determined based on the global routing table contents. Note that if the IP addresses on the R1/R2 and R1/R3 links are the same (or overlapping), there is no way of solving the connectivity problem without NAT.
Assuming that you are using 10.1.2.0/24 on the R1/R2 link, and 10.1.3.0/24 on the R1/R3 link, R1 would be configured as follows:
ip route 10.1.2.0 255.255.255.0 f2/0 ip route 10.1.3.0 255.255.255.0 g3/0Note that if R2 and R3 has also other networks behind themselves, for example, loopback networks (10.255.255.2/32 on R2, and 10.255.255.3/32 on R3), the additional configuration on R1 would be:
ip route 10.255.255.2 255.255.255.255 f2/0 10.1.2.2 ip route 10.255.255.3 255.255.255.255 g3/0 10.1.3.3The leaking from global routing table to a non-default VRF is done by referencing the egress interface - since that interface is a member of a single VRF, it also forces the packets to cross the VRF boundary.
There are two documents that also might be of interest (you likely know them but including them for completeness):
-
My VIRL sim got corrupted on save. I had to recreate it last night so the Sh run above is different now. I knew from the pings that nothing was crossing iosv-7 from flat to VRF. The ip routes below gave sh ip route the path to get to VRF.
iosv-7#sh run | s ip route
ip route 0.0.0.0 0.0.0.0 172.16.1.1
ip route 192.168.32.0 255.255.255.252 GigabitEthernet0/3
ip route 192.168.64.0 255.255.255.252 GigabitEthernet0/2
ip route vrf customer1 0.0.0.0 0.0.0.0 172.16.1.1 global
ip route vrf customer2 0.0.0.0 0.0.0.0 172.16.1.1 global
iosv-7#
iosv-7#iosv-1#
iosv-1#ping 172.16.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/4/7 ms
iosv-1#
iosv-1#I have never had to have routes pointing inward away from flat. Because VRF creates separate routing tables I had to add them.
-
Here is my rebuilt VRF sim.
I can ping to 172.16.1.1 from iosv-1 and iosv-2. I can't from 3 to 6. I have 172.16.16.x and 172.16.32.x on customer 1 and customer 2. So doing a static route to them would not be easy. Do I need some type of nat? I watched your video. I never saw you ping or your final configuration.
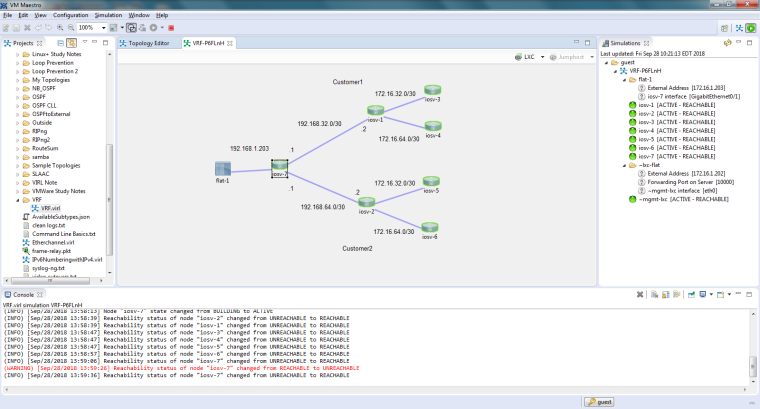
iosv-7#sh run
Building configuration...Current configuration : 4339 bytes
!
! Last configuration change at 13:58:47 UTC Fri Sep 28 2018
!
version 15.6
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname iosv-7
!
boot-start-marker
boot-end-marker
!
!
vrf definition Mgmt-intf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
enable password cisco
!
no aaa new-model
!
!
!
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
!
!
!
!
!
!
!
ip vrf customer1
!
ip vrf customer2
!
!
!
!
no ip domain lookup
ip domain name virl.info
ip cef
ipv6 unicast-routing
ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
username cisco privilege 15 secret 5 $1$pUcy$KqZNZ63JORbDOZXKRn2MF1
!
redundancy
!
no cdp run
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback0
description Loopback
no ip address
!
interface GigabitEthernet0/0
description OOB Management
vrf forwarding Mgmt-intf
ip address 10.255.7.71 255.255.0.0
duplex full
speed auto
media-type rj45
!
interface GigabitEthernet0/1
description to flat-1
ip address 172.16.1.203 255.255.255.0
duplex full
speed auto
media-type rj45
!
interface GigabitEthernet0/2
description to iosv-2
ip vrf forwarding customer2
ip address 192.168.64.1 255.255.255.252
ip ospf 2 area 0
duplex full
speed auto
media-type rj45
!
interface GigabitEthernet0/3
description to iosv-1
ip vrf forwarding customer1
ip address 192.168.32.1 255.255.255.252
ip ospf 1 area 0
duplex full
speed auto
media-type rj45
!
router ospf 2 vrf customer2
router-id 0.0.7.2
network 192.168.64.0 0.0.0.3 area 0
default-information originate always
!
router ospf 1 vrf customer1
router-id 0.0.7.1
network 192.168.32.0 0.0.0.3 area 0
default-information originate always
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 172.16.1.1
ip route 192.168.32.0 255.255.255.252 GigabitEthernet0/3
ip route 192.168.64.0 255.255.255.252 GigabitEthernet0/2
ip route vrf customer1 0.0.0.0 0.0.0.0 172.16.1.1 global
ip route vrf customer2 0.0.0.0 0.0.0.0 172.16.1.1 global
ip ssh server algorithm encryption aes128-ctr aes192-ctr aes256-ctr
ip ssh server algorithm authentication password
ip ssh client algorithm encryption aes128-ctr aes192-ctr aes256-ctr
!
ipv6 ioam timestamp
!
!
!
control-plane
!
banner exec ^C
- IOSv is strictly limited to use for evaluation, demonstration and IOS *
- education. IOSv is provided as-is and is not supported by Cisco's *
- Technical Advisory Center. Any use or disclosure, in whole or in part, *
- of the IOSv Software or Documentation to any third party for any *
- purposes is expressly prohibited except as otherwise authorized by *
- Cisco in writing. *
**************************************************************************^C
banner incoming ^C
- IOSv is strictly limited to use for evaluation, demonstration and IOS *
- education. IOSv is provided as-is and is not supported by Cisco's *
- Technical Advisory Center. Any use or disclosure, in whole or in part, *
- of the IOSv Software or Documentation to any third party for any *
- purposes is expressly prohibited except as otherwise authorized by *
- Cisco in writing. *
**************************************************************************^C
banner login ^C
- IOSv is strictly limited to use for evaluation, demonstration and IOS *
- education. IOSv is provided as-is and is not supported by Cisco's *
- Technical Advisory Center. Any use or disclosure, in whole or in part, *
- of the IOSv Software or Documentation to any third party for any *
- purposes is expressly prohibited except as otherwise authorized by *
- Cisco in writing. *
**************************************************************************^C
!
line con 0
password cisco
line aux 0
line vty 0 4
exec-timeout 720 0
password cisco
login local
transport input telnet ssh
!
no scheduler allocate
!
end
iosv-7#
-
If you want to ping frome customer 1 to customer 2 or vice versa. You may have to do some route redistribution across them If you're using a routing protocol.
I didn't do that on the show because we tried to keep the topic as as clean and limited to that single topic as possible. But that's what I've always used route redistribution to do it.
-
I changed the ip routes to /28 on iosv-7
I changed 192.168.32.x and 64.x to /28.
I setup NAT on iosv-1 and iosv-2
ip nat pool Cust1Top 192.168.32.4 192.168.32.4 netmask 255.255.255.0
ip nat pool Cust1Bot 192.168.32.5 192.168.32.5 netmask 255.255.255.0
ip nat inside source list 1 pool Cust1Top overload
ip nat inside source list 2 pool Cust1Bot overload
ip ssh server algorithm encryption aes128-ctr aes192-ctr aes256-ctr
ip ssh server algorithm authentication password
ip ssh client algorithm encryption aes128-ctr aes192-ctr aes256-ctr
!
ipv6 ioam timestamp
!
!
access-list 1 permit 172.16.32.0 0.0.0.3
access-list 2 permit 172.16.16.0 0.0.0.3
SO:
3 and 4 get NAT on 15 and 6 get NAT on 2
-
ip nat pool Cust2Top 192.168.64.3 192.168.64.3 netmask 255.255.255.0
ip nat pool Cust2Bot 192.168.64.4 192.168.64.4 netmask 255.255.255.0
ip nat inside source list 1 pool Cust2Top overload
ip nat inside source list 2 pool Cust2Bot overload
ip route 0.0.0.0 0.0.0.0 192.168.64.1
ip ssh server algorithm encryption aes128-ctr aes192-ctr aes256-ctr
ip ssh server algorithm authentication password
ip ssh client algorithm encryption aes128-ctr aes192-ctr aes256-ctr
!
ipv6 ioam timestamp
!
!
access-list 1 permit 172.16.32.0 0.0.0.3
access-list 2 permit 172.16.16.0 0.0.0.3 -
My problem with some of your content is the lack of completeness. Seems like you go 60-70% of the way there and leave the rest up to us to figure out. I used NAT and global routes to get it to work. Could you add a section for your sh run on each device so we can look at them after each show?
-
The problem again is that we covered NAT in a different episode already. On VRF, you normally don't seen it run unless you're in the service provider side of things. This show doesn't concentrate on the CCNP SP exams. So even with this, we would only see that full configuration as you've suggested from the Service Provider side.
On the episode, I configured two different VRFs, with two different sources and two separate hosts and ran the routing protocol for each VRF and showed it operationally working. Configuring VRF itself is not the objective here, It is only VRF-lite which is the focus of the episode. I try not to add complexity so that the focus is on setting up that topic and not explaining how everything else needs to work before it will work too. Hope this helps you to understand the process.
-
@ronnie-wong You are always a great help. When I took the CCNP exam a few months ago and failed it, it was a shock on how many questions were not in the books or videos on our site. I have been going through each topic and doing VIRL Sims on them. It would be great to see your finished sh runs with it working. Yes, I need to know one side of many topics for the CCNP. You can't get them properly working in a Sim without the other side done too.
-
https://wp.scsiraidguru.com/?page_id=1191
Here is the Simulation, Sh Run, Sh IP Route, Sh IP Route VRF files.
-
I like the new Cisco CCNP VRF-Lite Video done my Ronnie Wong. I hope my finished VRF project I attached using NAT with OSPF helps.
-
@michael-mckenney,
Thanks for sharing your lab! -
I thought it might help your users with the CCNP.
I started watching your new videos. I took your VRF-Lite video and did it for OSPF and working on EIGRP.. I am getting it so it can ping to the outside world from Cisco VIRL and going to work on getting TFTP to work with it.
I am watching your new VRF-Lite video. I saw you use 10.16.10.0 255.255.255.254. I had to look it up. I see it is described as a point to point connection. I love the new videos.
-
I watched Ronnie's new VRF-Lite video on CCNP Route. I did this simulation in Cisco VIRL
https://wp.scsiraidguru.com/?page_id=1239
This one is VRF-Lite with EIGRP. I am completing VRF-Lite for OSPF soon on my web site. It doesn't allow me to use default-information originate so I did a lot of ip route and ip route vrf statements to get in and out.
ip tftp source-interface g0/x allowed me to TFTP to my workstation.
sh run | redirect tftp://192.168.1.240/iosv1_ShRun.txt send iosv-1's sh run to a text file on my TFTP server. Speeds up building the simulations on my web page.

I added a few things for completeness. FLAT-1 connects to the 172.16.1..0 network on my Fortinet 60E. VIRL allows me to reach the real world. I setup IP TFTP source-interface g0/x to TFTP to my workstation.
172.16.1.1 is the 60E interface and 192.168.1.240 is my workstation.
I configured inbound and outbound IP routes for VRF to get to my workstation. Each router has loopbacks for HR and ACCT.
I did learn something new 10.16.10.0 / 255.255.255.254 is point to point.